Overview
- Kubernetes Cluster 구축을 위한 AWS 환경 구축 (Terraform)
[AWS] Rancher를 통한 Kubernetes 클러스터 구축
Overview AWS 환경에서 Rancher를 통한 Kubernetes 클러스터 구축하기 AWS 환경에서 구축을 진행하지만, 베어 메탈 및 다양한 클라우드 플랫폼에서 적용 가능합니다. Architecture AWS 환경VPC 구성 - 가용 영
taronko.tistory.com
Architecture
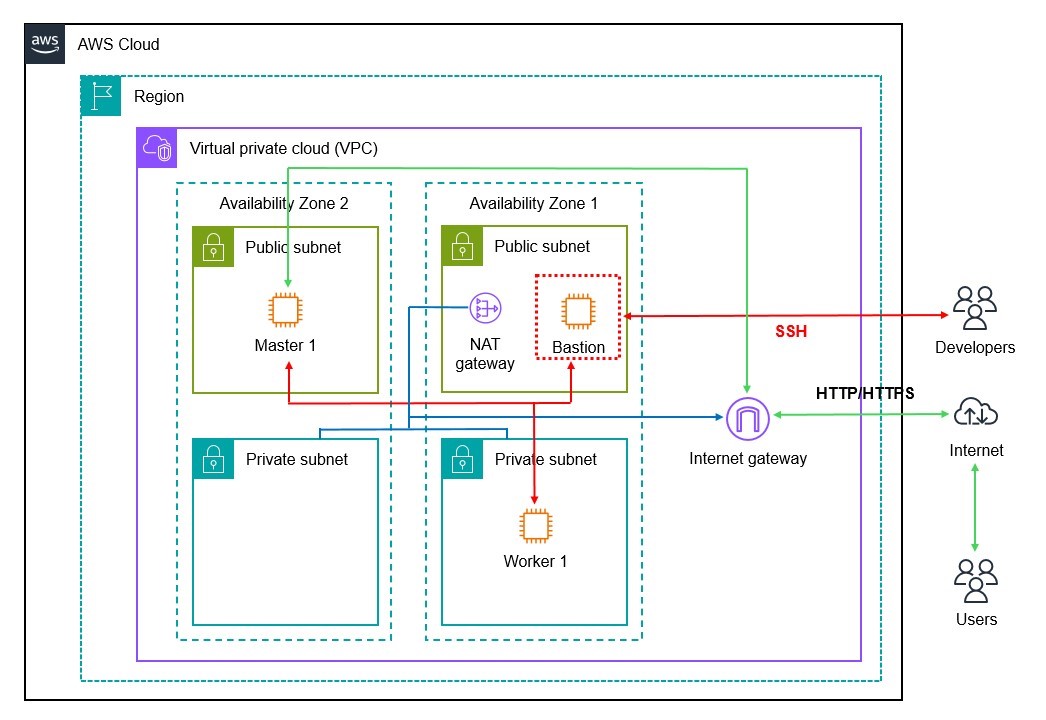
Prerequisite
1. Terraform 설치 (링크)
// 기본 명령어
* terraform init
* terraform plan
* terraform apply
* terraform destroy
2. AWS 계정
3. AWS IAM 사용자 (관리자) 생성
- AdministratorAccess로 간단하게 생성
4. 로컬 환경 변수
- 3번에서 생성한 관리자의 Access Key와 Secret Key를 로컬 환경 변수에 저장
// AWS IAM 정보 (Windows)
$Env:AWS_ACCESS_KEY_ID=""
$Env:AWS_SECRET_ACCESS_KEY=""// AWS IAM 정보 (Mac OS)
export AWS_ACCESS_KEY_ID=""
export AWS_SECRET_ACCESS_KEY=""
AWS Infra Provisioning
1. 전체 코드는 아래 'Code Description' 참고
2. Source Tree는 아래와 같다.
env
ㄴ dev
ㄴ ec2.tf
ㄴ eip.tf
ㄴ iam.tf
ㄴ key_fair.tf
ㄴ main.tf
ㄴ security_groups.tf
ㄴ variables.tf
ㄴ vpc.tf
3. Provisioning
$ cd env/dev/
$ terraform init
$ terraform plan
$ terraform apply
4. AWS에서 리소스 생성 확인(Architecture 확인) 및 EC2 접속 테스트
// 방법 1
// AWS > Elastic IP > 'k8s-dev-master-eip-1' IP
$ ping {Master Node EIP}
// 방법 2
// 로컬에 생성된 키로 EC2 인스턴스에 접속
// SSH 접속 (private-ec2-worker-key.pem, public-ec2-bastion-key.pem, public-ec2-master-key.pem)
$ ssh -i {*-key.pem} ubuntu@{ip}
5. AWS 리소스 제거
// 실습 후 리소스 제거
$ cd env/dev/
$ terraform destroy
Code Description
1. env/dev/main.tf
* Provider 설정 (AWS)
* Region 설정
terraform {
required_providers {
aws = {
source = "hashicorp/aws"
version = "~> 5.0"
}
}
}
# Configure the AWS Provider
provider "aws" {
region = "ap-northeast-2"
}
2. env/dev/variables.tf
* 변수값 설정
# Project
variable "project_name" { default = "k8s" }
variable "environment" { default = "dev" }
# VPC
variable "cidr_vpc" { default = "10.0.0.0/16"}
variable "cidr_public_1" { default = "10.0.0.0/24" }
variable "cidr_public_2" { default = "10.0.1.0/24" }
variable "cidr_private_1" { default = "10.0.10.0/24" }
variable "cidr_private_2" { default = "10.0.11.0/24" }
# Public EC2 (Bastion)
variable "public_ec2_bastion_ami" { default = "ami-01ed8ade75d4eee2f" }
variable "public_ec2_bastion_instance_type" { default = "t2.medium" }
variable "public_ec2_bastion_key_name" { default = "public-ec2-bastion-key.pem" }
variable "public_ec2_bastion_volume_size" { default = 16 }
# Public EC2 (Master)
variable "public_ec2_master_ami" { default = "ami-01ed8ade75d4eee2f" }
variable "public_ec2_master_instance_type" { default = "t2.medium" }
variable "public_ec2_master_key_name" { default = "public-ec2-master-key.pem" }
variable "public_ec2_master_volume_size" { default = 8 }
# Private EC2 (Worker)
variable "private_ec2_worker_ami" { default = "ami-01ed8ade75d4eee2f" }
variable "private_ec2_worker_instance_type" { default = "t2.medium" }
variable "private_ec2_worker_key_name" { default = "private-ec2-worker-key.pem" }
variable "private_ec2_worker_volume_size" { default = 8 }
3. env/dev/eip.tf
* Elastic IP 설정
# Elastic IP
## Public EC2 (Bastion)
resource "aws_eip" "public-ec2-bastion-eip" {
instance = aws_instance.public-ec2-bastion.id
tags = {
Name = "${var.project_name}-${var.environment}-bastion-eip"
}
}
## Public EC2 (Master)
resource "aws_eip" "public-ec2-master-eip-1" {
instance = aws_instance.public-ec2-master-1.id
tags = {
Name = "${var.project_name}-${var.environment}-master-eip-1"
}
}
## NAT Gateway
resource "aws_eip" "nat-gateway-eip" {
depends_on = [aws_internet_gateway.internet-gateway]
tags = {
Name = "${var.project_name}-${var.environment}-nat-gateway-eip"
}
}
4. env/dev/ec2.tf
* EC2 생성
# Public EC2
## Public EC2 (Bastion)
resource "aws_instance" "public-ec2-bastion" {
ami = "${var.public_ec2_bastion_ami}"
instance_type = "${var.public_ec2_bastion_instance_type}"
vpc_security_group_ids = [aws_security_group.public-ec2-bastion-security-group.id]
iam_instance_profile = aws_iam_instance_profile.bastion-iam-instance-profile.name
subnet_id = aws_subnet.public-subnet-1.id
key_name = "${var.public_ec2_bastion_key_name}"
disable_api_termination = false
root_block_device {
volume_size = "${var.public_ec2_bastion_volume_size}"
volume_type = "gp3"
delete_on_termination = true
tags = {
Name = "${var.project_name}-${var.environment}-public-ec2-bastion"
}
}
tags = {
Name = "${var.project_name}-${var.environment}-public-ec2-bastion"
}
}
## Public EC2 (Master)
resource "aws_instance" "public-ec2-master-1" {
ami = "${var.public_ec2_master_ami}"
instance_type = "${var.public_ec2_master_instance_type}"
vpc_security_group_ids = [aws_security_group.public-ec2-master-security-group.id]
iam_instance_profile = aws_iam_instance_profile.master-iam-instance-profile.name
subnet_id = aws_subnet.public-subnet-2.id
key_name = "${var.public_ec2_master_key_name}"
disable_api_termination = false
root_block_device {
volume_size = "${var.public_ec2_master_volume_size}"
volume_type = "gp3"
delete_on_termination = true
tags = {
Name = "${var.project_name}-${var.environment}-public-ec2-master-1"
}
}
tags = {
Name = "${var.project_name}-${var.environment}-public-ec2-master-1"
}
}
# Prviate EC2
## Prviate EC2 (Worker)
resource "aws_instance" "private-ec2-worker-1" {
ami = "${var.private_ec2_worker_ami}"
instance_type = "${var.private_ec2_worker_instance_type}"
vpc_security_group_ids = [aws_security_group.private-ec2-worker-security-group.id]
iam_instance_profile = aws_iam_instance_profile.worker-iam-instance-profile.name
subnet_id = aws_subnet.private-subnet-1.id
associate_public_ip_address = false
key_name = "${var.private_ec2_worker_key_name}"
disable_api_termination = false
root_block_device {
volume_size = "${var.private_ec2_worker_volume_size}"
volume_type = "gp3"
delete_on_termination = true
tags = {
Name = "${var.project_name}-${var.environment}-private-ec2-worker-1"
}
}
tags = {
Name = "${var.project_name}-${var.environment}-private-ec2-worker-1"
}
}
5. env/dev/iam.tf
* EC2 권한 설정
data "aws_iam_policy_document" "iam-policy-document-assume-role" {
statement {
actions = ["sts:AssumeRole"]
principals {
type = "Service"
identifiers = ["ec2.amazonaws.com"]
}
}
}
data "aws_iam_policy" "iam-policy-system-manager" {
arn = "arn:aws:iam::aws:policy/AmazonSSMManagedInstanceCore"
}
data "aws_iam_policy" "iam-policy-cloudwatch-agent" {
arn = "arn:aws:iam::aws:policy/CloudWatchAgentAdminPolicy"
}
# IAM Role
## Public EC2 (Bastion)
resource "aws_iam_role" "public-ec2-bastion-iam-role" {
name = "${var.project_name}-${var.environment}-bastion-iam-role"
assume_role_policy = data.aws_iam_policy_document.iam-policy-document-assume-role.json
}
resource "aws_iam_role_policy_attachment" "bastion-iam-role-policy-attachment-system-manager" {
role = aws_iam_role.public-ec2-bastion-iam-role.name
policy_arn = data.aws_iam_policy.iam-policy-system-manager.arn
}
resource "aws_iam_role_policy_attachment" "bastion-iam-role-policy-attachment-cloudwatch-agent" {
role = aws_iam_role.public-ec2-bastion-iam-role.name
policy_arn = data.aws_iam_policy.iam-policy-cloudwatch-agent.arn
}
resource "aws_iam_instance_profile" "bastion-iam-instance-profile" {
name = "${var.project_name}-${var.environment}-bastion-iam-instance-profile"
role = aws_iam_role.public-ec2-bastion-iam-role.name
}
## Public EC2 (Master)
resource "aws_iam_role" "public-ec2-master-iam-role" {
name = "${var.project_name}-${var.environment}-master-iam-role"
assume_role_policy = data.aws_iam_policy_document.iam-policy-document-assume-role.json
}
resource "aws_iam_role_policy_attachment" "master-iam-role-policy-attachment-system-manager" {
role = aws_iam_role.public-ec2-master-iam-role.name
policy_arn = data.aws_iam_policy.iam-policy-system-manager.arn
}
resource "aws_iam_role_policy_attachment" "master-iam-role-policy-attachment-cloudwatch-agent" {
role = aws_iam_role.public-ec2-master-iam-role.name
policy_arn = data.aws_iam_policy.iam-policy-cloudwatch-agent.arn
}
resource "aws_iam_instance_profile" "master-iam-instance-profile" {
name = "${var.project_name}-${var.environment}-master-iam-instance-profile"
role = aws_iam_role.public-ec2-master-iam-role.name
}
## Prviate EC2 (Worker)
resource "aws_iam_role" "private-ec2-worker-iam-role" {
name = "${var.project_name}-${var.environment}-worker-iam-role"
assume_role_policy = data.aws_iam_policy_document.iam-policy-document-assume-role.json
}
resource "aws_iam_role_policy_attachment" "worker-iam-role-policy-attachment-system-manager" {
role = aws_iam_role.private-ec2-worker-iam-role.name
policy_arn = data.aws_iam_policy.iam-policy-system-manager.arn
}
resource "aws_iam_role_policy_attachment" "worker-iam-role-policy-attachment-cloudwatch-agent" {
role = aws_iam_role.private-ec2-worker-iam-role.name
policy_arn = data.aws_iam_policy.iam-policy-cloudwatch-agent.arn
}
resource "aws_iam_instance_profile" "worker-iam-instance-profile" {
name = "${var.project_name}-${var.environment}-worker-iam-instance-profile"
role = aws_iam_role.private-ec2-worker-iam-role.name
}
6. env/dev/key_fair.tf
* Key Fair 생성
EC2 생성 시 필요한 Key Fair 생성. 이후, EC2에 ssh 접속할 때 필요
# Key Fair
## Public Key Fair (Bastion)
resource "tls_private_key" "public-ec2-bastion-key" {
algorithm = "RSA"
rsa_bits = 4096
}
resource "aws_key_pair" "public-ec2-bastion-key-fair" {
key_name = "${var.public_ec2_bastion_key_name}"
public_key = tls_private_key.public-ec2-bastion-key.public_key_openssh
}
resource "local_file" "public-ec2-bastion-key-fair-local" {
filename = "${var.public_ec2_bastion_key_name}"
content = tls_private_key.public-ec2-bastion-key.private_key_pem
file_permission = "0600"
}
## Public Key Fair (Master)
resource "tls_private_key" "public-ec2-master-key" {
algorithm = "RSA"
rsa_bits = 4096
}
resource "aws_key_pair" "public-ec2-master-key-fair" {
key_name = "${var.public_ec2_master_key_name}"
public_key = tls_private_key.public-ec2-master-key.public_key_openssh
}
resource "local_file" "public-ec2-master-key-fair-local" {
filename = "${var.public_ec2_master_key_name}"
content = tls_private_key.public-ec2-master-key.private_key_pem
file_permission = "0600"
}
## Private Key Fair (Worker)
resource "tls_private_key" "private-ec2-worker-key" {
algorithm = "RSA"
rsa_bits = 4096
}
resource "aws_key_pair" "private-ec2-worker-key-fair" {
key_name = "${var.private_ec2_worker_key_name}"
public_key = tls_private_key.private-ec2-worker-key.public_key_openssh
}
resource "local_file" "private-ec2-worker-key-fair-local" {
filename = "${var.private_ec2_worker_key_name}"
content = tls_private_key.private-ec2-worker-key.private_key_pem
file_permission = "0600"
}
7. env/dev/security_groups.tf
* EC2 Security Group 생성
인바운드, 아웃바운드 규칙 설정
RKE2 Port 참고 (링크)
# Security Group
## Public EC2 (Bastion)
resource "aws_security_group" "public-ec2-bastion-security-group"{
name = "${var.project_name}-${var.environment}-bastion-security-group"
vpc_id = aws_vpc.vpc.id
tags = {
Name = "${var.project_name}-${var.environment}-bastion-security-group"
}
}
## Public EC2 (Master)
resource "aws_security_group" "public-ec2-master-security-group"{
name = "${var.project_name}-${var.environment}-master-security-group"
vpc_id = aws_vpc.vpc.id
tags = {
Name = "${var.project_name}-${var.environment}-master-security-group"
}
}
## Private EC2 (Worker)
resource "aws_security_group" "private-ec2-worker-security-group"{
name = "${var.project_name}-${var.environment}-worker-security-group"
vpc_id = aws_vpc.vpc.id
tags = {
Name = "${var.project_name}-${var.environment}-worker-security-group"
}
}
# Ingress Rules
## Public EC2 (Bastion) - Ingress Rules - 22 (SSH)
resource "aws_security_group_rule" "public-ec2-bastion-security-group-rule-ingress-22" {
type = "ingress"
from_port = 22
to_port = 22
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
security_group_id = aws_security_group.public-ec2-bastion-security-group.id
}
## Public EC2 (Bastion) - Ingress Rules - 443 (Https)
resource "aws_security_group_rule" "public-ec2-bastion-security-group-rule-ingress-443" {
type = "ingress"
from_port = 443
to_port = 443
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
security_group_id = aws_security_group.public-ec2-bastion-security-group.id
}
## Public EC2 (Bastion) - Ingress Rules - 3000 (Gitea)
resource "aws_security_group_rule" "public-ec2-bastion-security-group-rule-ingress-3000" {
type = "ingress"
from_port = 3000
to_port = 3000
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
security_group_id = aws_security_group.public-ec2-bastion-security-group.id
}
## Public EC2 (Bastion) - Ingress Rules - 5000 (Nexus)
resource "aws_security_group_rule" "public-ec2-bastion-security-group-rule-ingress-5000" {
type = "ingress"
from_port = 5000
to_port = 5000
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
security_group_id = aws_security_group.public-ec2-bastion-security-group.id
}
## Public EC2 (Bastion) - Ingress Rules - 8081 (Nexus)
resource "aws_security_group_rule" "public-ec2-bastion-security-group-rule-ingress-8081" {
type = "ingress"
from_port = 8081
to_port = 8081
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
security_group_id = aws_security_group.public-ec2-bastion-security-group.id
}
## Public EC2 (Master) - Ingress Rules - 22 (SSH)
resource "aws_security_group_rule" "public-ec2-master-security-group-rule-ingress-22" {
type = "ingress"
from_port = 22
to_port = 22
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
security_group_id = aws_security_group.public-ec2-master-security-group.id
}
## Public EC2 (Master) - Ingress Rules - RKE2 server and agent nodes (Node registration. Port should be open on all server nodes to all other nodes in the cluster.)
resource "aws_security_group_rule" "public-ec2-master-security-group-rule-ingress-9345" {
type = "ingress"
from_port = 9345
to_port = 9345
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
security_group_id = aws_security_group.public-ec2-master-security-group.id
}
## Public EC2 (Master) - Ingress Rules - RKE2 agent nodes (Kubernetes API)
resource "aws_security_group_rule" "public-ec2-master-security-group-rule-ingress-6443" {
type = "ingress"
from_port = 6443
to_port = 6443
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
security_group_id = aws_security_group.public-ec2-master-security-group.id
}
## Public EC2 (Master) - Ingress Rules - RKE2 server and agent nodes (Required only for Flannel VXLAN)
resource "aws_security_group_rule" "public-ec2-master-security-group-rule-ingress-8472" {
type = "ingress"
from_port = 8472
to_port = 8472
protocol = "udp"
cidr_blocks = ["0.0.0.0/0"]
security_group_id = aws_security_group.public-ec2-master-security-group.id
}
## Public EC2 (Master) - Ingress Rules - RKE2 server and agent nodes (kubelet)
resource "aws_security_group_rule" "public-ec2-master-security-group-rule-ingress-10250" {
type = "ingress"
from_port = 10250
to_port = 10250
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
security_group_id = aws_security_group.public-ec2-master-security-group.id
}
## Public EC2 (Master) - Ingress Rules - RKE2 server nodes (etcd client port)
resource "aws_security_group_rule" "public-ec2-master-security-group-rule-ingress-2379" {
type = "ingress"
from_port = 2379
to_port = 2379
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
security_group_id = aws_security_group.public-ec2-master-security-group.id
}
## Public EC2 (Master) - Ingress Rules - RKE2 server nodes (etcd peer port)
resource "aws_security_group_rule" "public-ec2-master-security-group-rule-ingress-2380" {
type = "ingress"
from_port = 2380
to_port = 2380
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
security_group_id = aws_security_group.public-ec2-master-security-group.id
}
## Public EC2 (Master) - Ingress Rules - Calico-node pod connecting to typha pod (Required when deploying with Calico)
resource "aws_security_group_rule" "public-ec2-master-security-group-rule-ingress-5473" {
type = "ingress"
from_port = 5473
to_port = 5473
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
security_group_id = aws_security_group.public-ec2-master-security-group.id
}
## Public EC2 (Master) - Ingress Rules - 80 (Http)
resource "aws_security_group_rule" "public-ec2-master-security-group-rule-ingress-80" {
type = "ingress"
from_port = 80
to_port = 80
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
security_group_id = aws_security_group.public-ec2-master-security-group.id
}
## Public EC2 (Master) - Ingress Rules - 443 (Https)
resource "aws_security_group_rule" "public-ec2-master-security-group-rule-ingress-443" {
type = "ingress"
from_port = 443
to_port = 443
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
security_group_id = aws_security_group.public-ec2-master-security-group.id
}
## Public EC2 (Master) - Ingress Rules - ICMP
resource "aws_security_group_rule" "public-ec2-master-security-group-rule-ingress-icmp" {
type = "ingress"
from_port = -1
to_port = -1
protocol = "icmp"
cidr_blocks = ["0.0.0.0/0"]
security_group_id = aws_security_group.public-ec2-master-security-group.id
}
## Prviate EC2 (Worker) - Ingress Rules - 22 (SSH)
resource "aws_security_group_rule" "private-ec2-worker-security-group-rule-ingress-22" {
type = "ingress"
from_port = 22
to_port = 22
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
security_group_id = aws_security_group.private-ec2-worker-security-group.id
}
## Prviate EC2 (Worker) - Ingress Rules - RKE2 server and agent nodes (Node registration. Port should be open on all server nodes to all other nodes in the cluster.)
resource "aws_security_group_rule" "private-ec2-worker-security-group-rule-ingress-9345" {
type = "ingress"
from_port = 9345
to_port = 9345
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
security_group_id = aws_security_group.private-ec2-worker-security-group.id
}
## Prviate EC2 (Worker) - Ingress Rules - RKE2 agent nodes (Kubernetes API)
resource "aws_security_group_rule" "private-ec2-worker-security-group-rule-ingress-6443" {
type = "ingress"
from_port = 6443
to_port = 6443
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
security_group_id = aws_security_group.private-ec2-worker-security-group.id
}
## Prviate EC2 (Worker) - Ingress Rules - RKE2 server and agent nodes (Required only for Flannel VXLAN)
resource "aws_security_group_rule" "private-ec2-worker-security-group-rule-ingress-8472" {
type = "ingress"
from_port = 8472
to_port = 8472
protocol = "udp"
cidr_blocks = ["0.0.0.0/0"]
security_group_id = aws_security_group.private-ec2-worker-security-group.id
}
## Prviate EC2 (Worker) - Ingress Rules - RKE2 server and agent nodes (kubelet)
resource "aws_security_group_rule" "private-ec2-worker-security-group-rule-ingress-10250" {
type = "ingress"
from_port = 10250
to_port = 10250
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
security_group_id = aws_security_group.private-ec2-worker-security-group.id
}
## Prviate EC2 (Worker) - Ingress Rules - Calico-node pod connecting to typha pod (Required when deploying with Calico)
resource "aws_security_group_rule" "private-ec2-worker-security-group-rule-ingress-5473" {
type = "ingress"
from_port = 5473
to_port = 5473
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
security_group_id = aws_security_group.private-ec2-worker-security-group.id
}
# Egress Rules
## Public EC2 (Bastion) - Egress Rules - Anywhere
resource "aws_security_group_rule" "public-ec2-bastion-security-group-rule-egress-anywhere" {
type = "egress"
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
security_group_id = aws_security_group.public-ec2-bastion-security-group.id
}
## Public EC2 (Master) - Egress Rules - Anywhere
resource "aws_security_group_rule" "public-ec2-master-security-group-rule-egress-anywhere" {
type = "egress"
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
security_group_id = aws_security_group.public-ec2-master-security-group.id
}
## Private EC2 (Worker) - Egress Rules - Anywhere
resource "aws_security_group_rule" "public-ec2-worker-security-group-rule-egress-anywhere" {
type = "egress"
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
security_group_id = aws_security_group.private-ec2-worker-security-group.id
}
8. env/dev/vpc.tf
* VPC 설정
# VPC
resource "aws_vpc" "vpc" {
cidr_block = "${var.cidr_vpc}"
enable_dns_support = true
enable_dns_hostnames = true
tags = {
Name = "${var.project_name}-${var.environment}-vpc"
}
}
# Internet Gateway
resource "aws_internet_gateway" "internet-gateway" {
vpc_id = aws_vpc.vpc.id
tags = {
Name = "${var.project_name}-${var.environment}-internet-gateway"
}
}
# NAT Gateway
resource "aws_nat_gateway" "nat-gateway" {
allocation_id = aws_eip.nat-gateway-eip.id
subnet_id = aws_subnet.public-subnet-1.id
depends_on = [aws_internet_gateway.internet-gateway]
tags = {
Name = "${var.project_name}-${var.environment}-nat-gateway"
}
}
# Subnet
## Public Subnet 1
resource "aws_subnet" "public-subnet-1" {
vpc_id = aws_vpc.vpc.id
availability_zone = "ap-northeast-2a"
cidr_block = "${var.cidr_public_1}"
map_public_ip_on_launch = true
tags = {
Name = "${var.project_name}-${var.environment}-public-subnet-1"
}
}
## Public Subnet 2
resource "aws_subnet" "public-subnet-2" {
vpc_id = aws_vpc.vpc.id
availability_zone = "ap-northeast-2c"
cidr_block = "${var.cidr_public_2}"
map_public_ip_on_launch = true
tags = {
Name = "${var.project_name}-${var.environment}-public-subnet-2"
}
}
## Private Subnet 1
resource "aws_subnet" "private-subnet-1" {
vpc_id = aws_vpc.vpc.id
availability_zone = "ap-northeast-2a"
cidr_block = "${var.cidr_private_1}"
map_public_ip_on_launch = false
tags = {
Name = "${var.project_name}-${var.environment}-private-subnet-1"
}
}
## Private Subnet 2
resource "aws_subnet" "private-subnet-2" {
vpc_id = aws_vpc.vpc.id
availability_zone = "ap-northeast-2c"
cidr_block = "${var.cidr_private_2}"
map_public_ip_on_launch = false
tags = {
Name = "${var.project_name}-${var.environment}-private-subnet-2"
}
}
# Route table
## Public Route Table
resource "aws_route_table" "public-route-table" {
vpc_id = aws_vpc.vpc.id
tags = {
Name = "${var.project_name}-${var.environment}-public-route-table"
}
}
## Public Route Table Association 1
resource "aws_route_table_association" "public-route-table-association-1" {
subnet_id = aws_subnet.public-subnet-1.id
route_table_id = aws_route_table.public-route-table.id
}
## Public Route Table Association 2
resource "aws_route_table_association" "public-route-table-association-2" {
subnet_id = aws_subnet.public-subnet-2.id
route_table_id = aws_route_table.public-route-table.id
}
## Public Route
resource "aws_route" "public-route" {
route_table_id = aws_route_table.public-route-table.id
gateway_id = aws_internet_gateway.internet-gateway.id
destination_cidr_block = "0.0.0.0/0"
}
## Private Route Table
resource "aws_route_table" "private-route-table" {
vpc_id = aws_vpc.vpc.id
tags = {
Name = "${var.project_name}-${var.environment}-private-route-table"
}
}
## Private Route Table Association 1
resource "aws_route_table_association" "private-route-table-association-1" {
subnet_id = aws_subnet.private-subnet-1.id
route_table_id = aws_route_table.private-route-table.id
}
## Private Route Table Association 2
resource "aws_route_table_association" "private-route-table-association-2" {
subnet_id = aws_subnet.private-subnet-2.id
route_table_id = aws_route_table.private-route-table.id
}
## Private Route
resource "aws_route" "private-route" {
route_table_id = aws_route_table.private-route-table.id
nat_gateway_id = aws_nat_gateway.nat-gateway.id
destination_cidr_block = "0.0.0.0/0"
}
# NACL
## Public Network ACL
resource "aws_network_acl" "public-network-acl" {
vpc_id = aws_vpc.vpc.id
subnet_ids = [aws_subnet.public-subnet-1.id, aws_subnet.private-subnet-2.id]
egress {
protocol = -1
rule_no = 100
action = "allow"
cidr_block = "0.0.0.0/0"
from_port = 0
to_port = 0
}
ingress {
protocol = -1
rule_no = 100
action = "allow"
cidr_block = "0.0.0.0/0"
from_port = 0
to_port = 0
}
tags = {
Name = "${var.project_name}-${var.environment}-public-network-acl"
}
}
## Private Network ACL
resource "aws_network_acl" "private-network-acl" {
vpc_id = aws_vpc.vpc.id
subnet_ids = [aws_subnet.private-subnet-1.id, aws_subnet.private-subnet-2.id]
egress {
protocol = -1
rule_no = 100
action = "allow"
cidr_block = "0.0.0.0/0"
from_port = 0
to_port = 0
}
ingress {
protocol = -1
rule_no = 100
action = "allow"
cidr_block = "0.0.0.0/0"
from_port = 0
to_port = 0
}
tags = {
Name = "${var.project_name}-${var.environment}-private-network-acl"
}
}'IaC' 카테고리의 다른 글
| [IaC] Ansible을 통한 Application 구축 자동화 (3) | 2024.06.20 |
|---|